How to Fix Error 525 - SSL Handshake failed with LetsEncrypt and Laravel Forge
If you're anything like us, you use Laravel Forge to provision your servers and LetsEncrypt SSL certificates. After all, it's the defau...
If you're anything like us, you use Laravel Forge to provision your servers and LetsEncrypt SSL certificates. After all, it's the defau...
If you're anything like us, you use Laravel Forge to provision your servers and LetsEncrypt SSL certificates. After all, it's the default way to do it, and it works out-of-the-box. The setup has worked great for us, for years.
But today, out of the blue, a bunch of our properties have gone down, showing either Error 525 - SSL Handshake Failed (if ran through CloudFlare) or straight up This site can't provide a secure connection, more specifically ERR_SSL_VERSION_OR_CIPHER_MISMATCH.
In hindsight, it should have been an easy fix, but we scratched our head quite a bit to fix this. We hope posting this here will save you some pain.
Our problem, turns out, was that our NGINX configurations for those properties were a bit outdated, didn't support some TLS versions and more importantly, didn't support many ciphers.
To verify and fix this, on a site's page in Laravel Forge, go to the very bottom, and under "Files" you'll find the NGINX configuration file, and be able to edit it.
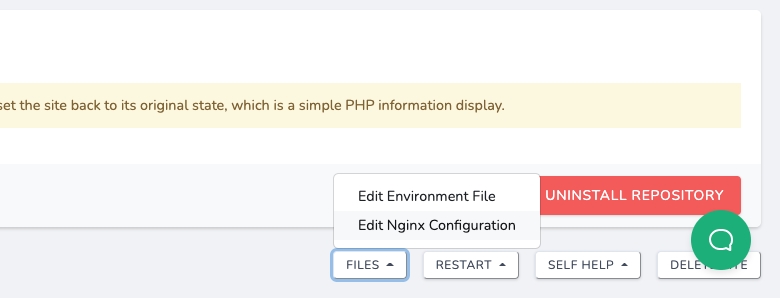
For us, it was as simple as adding more CloudFlare-supported ciphers to the list, but you might also want to enable other TLS versions.
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name app.somedomain.com;
root /home/forge/app.somedomain.com/public;
# FORGE SSL (DO NOT REMOVE!)
ssl_certificate /etc/nginx/ssl/app.somedomain.com/1111111/server.crt;
ssl_certificate_key /etc/nginx/ssl/app.somedomain.com/1111111/server.key;
- ssl_protocols TLSv1.2;
- ssl_ciphers ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384;
+ ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
+ ssl_ciphers TLS13-AES-256-GCM-SHA384:TLS13-CHACHA20-POLY1305-SHA256:TLS_AES_256_GCM_SHA384:TLS-AES-256-GCM-SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS-CHACHA20-POLY1305-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA;
After you save the file, make sure that the message says "configuration is valid" or "configuration successful". Otherwise you might need to only add ciphers without bumping TLS versions.
Hopefully it'll save you some trouble.
PS. Alternatively, here are some other ciphers that worked for us when dealing with CloudFlare as DNS and proxy:
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA:!3DES';
Subscribe to our "Article Digest". We'll send you a list of the new articles, every week, month or quarter - your choice.
What do you think about this?
Wondering what our community has been up to?