We recommend you fix this vulnerability
We regularly conduct private security audits of our software. Unlike most times, in March 2022 we’ve discovered a security issue that m...
We regularly conduct private security audits of our software. Unlike most times, in March 2022 we’ve discovered a security issue that m...
We regularly conduct private security audits of our software. Unlike most times, in March 2022 we’ve discovered a security issue that might affect you.
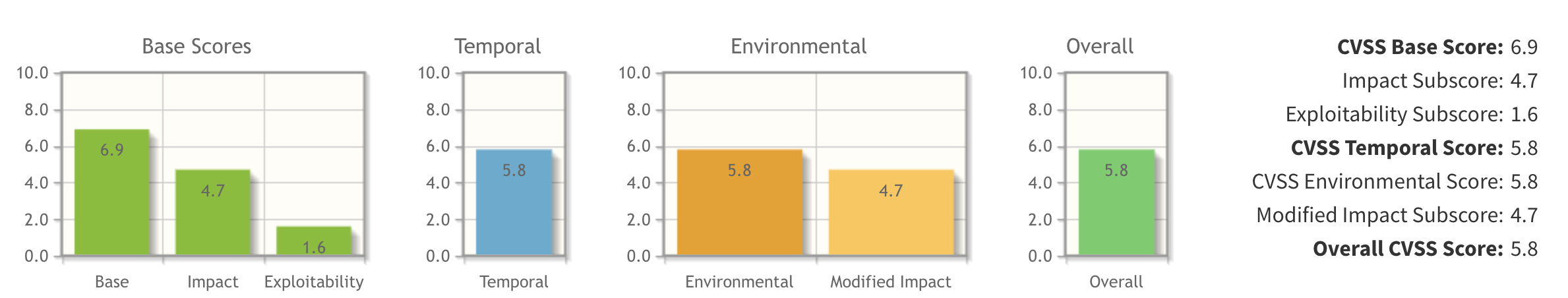
It’s a “moderate” vulnerability… but being an admin panel, we take this seriously. It’s difficult… but an attacker could conduct a targeted phishing campaign, in order to trick your users or admins to click a malicious link, which under very specific circumstances could give them information... or even admin access. It’s unlikely, but that’s not good enough in admin panels - we should make it impossible. That’s why we’re bothering you with this.
If you haven't already fixed this, we recommend fixing it now. It takes one minute.
If you don’t have custom error views, the views provided by Backpack will output the exception message without escaping it, which makes an attack possible using Reflected XSS, in some very specific circumstances (that we will not disclose). To fix those error views in Backpack 4.x and 5.x, please run:
composer update backpack/crud
php artisan backpack:fix
Alternatively (if you don’t want to run composer update), you can manually look inside your error views in “resources/views/errors” and output e($exception->getMessage()) instead of $exception->getMessage(). That’s all there is to the fix, really.
Of course, new installations do not have this vulnerability.
We’ve acted as soon as our team found it (last week of March 2022):
php artisan backpack:fix command;We’re writing this blog post to admit our fault, tell you we fixed it and show you we’ve got your back. We’re regularly conducting these security audits, to double-check and triple-check our software. Thanks to them, we discovered this ourselves, before anybody else.
Again, we’re sorry this has slipped through. We hope this shows that even if we make mistakes, we own them, repair them and tell you about them. Thank you for your trust.
Please do the fix above, it’s super-easy. Cheers!
Subscribe to our "Article Digest". We'll send you a list of the new articles, every week, month or quarter - your choice.
What do you think about this?
Wondering what our community has been up to?